Enterprise Data Communication Security Solution Based on 3G Network
With the continuous popularization of 3G network services, operators have launched 3G VPDN (Virtual Private Dial-Network) services to meet the needs of enterprise users for "3G mobile private networks", that is, virtual private dial-up networks based on 3G wireless access methods For business, it uses the L2TP tunnel transmission protocol to build a virtual private channel on the existing dial-up network without interference from the outside world, so as to achieve similar access to corporate intranet resources by using a wired private network.
Data communication equipment manufacturers have also launched 3G routers in time to adapt to this application trend of industry users. Enterprise networks have entered the era of 3G networking.
When there are many network outlets such as finance and government, and there are a large number of industrial users who have the needs of off-line ATM access, remote township access and mobile network access, they also turn their attention to 3G access, and carry out enterprise data communication based on 3G network. Security has become the biggest obstacle to the large-scale application of 3G networks in these industries that require high data security.
3G network data communication application overview
3G-based data communication applications have the following networking modes:
1. Access the internet
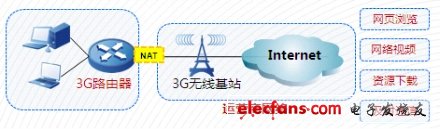
Figure 1 access to the internet
The 3G router is configured with a 3G module, uses a common APN name, user name and password, accesses the Internet network through the operator ’s wireless base station, and configures NAT address translation. The 3G router intranet PC accesses public network resources through the 3G network, such as web browsing, public Online mailbox, timely communication, network download and other resources.
2. Internet + VPN tunnel
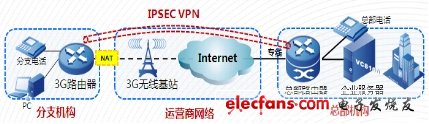
Figure 2 Internte + VPN tunnel
The 3G router is configured with a 3G module, uses a common APN name, user name and password, and accesses the Internet network through the use of wireless base stations. For data streams that require access to public network resources, after configuring NAT address translation, it directly communicates with the Internet. For data streams that require access to the headquarters' private network resources (such as company VOIP voice calls, video conferencing systems, internal office OA systems, etc.), direct communication is performed through the 3G router and the Ipsec VPN encrypted tunnel established by the headquarters router.
3. 3G VPDN private network

Figure 3 3G VPDN private network
As shown in the figure above, in order to ensure the business security requirements of 3G access networks for major corporate customers, operators can provide users with dedicated line APN (Access Point Name) transmission methods, provide users with dedicated access point names, and can provide user names and passwords , IMSI's multiple security authentication function. LNS connects the headquarters equipment (router, VPN equipment) of the user to the operator's network through a dedicated line. The 3G router at the branch network is equipped with a 3G module. The enterprise uses the dedicated APN name and user name password applied by the enterprise to access the 3G network. After the name or user name and password determine that the user is an enterprise private network user, the LAC device triggers the L2TP authentication negotiation with the user-side LNS device, and the LNS device finally allocates the private network IP address to the branch network 3G router to achieve the branch network. Interworking with the private line of the headquarters private network.
Based on the 3G VPDN private network is the model that operators mainly promote for industry users. This article will focus on the analysis of the security deployment of applications based on the 3G VPDN private network. First, let's take a look at the security mechanisms of 3G wireless.
3G Wireless Security Introduction
The characteristic of wireless communication itself is that it is easy for legal users to access and easy to be stolen by potential illegal users. Therefore, security issues are always closely related to mobile communication networks.
In response to the security problems in wireless communication, the 3G system has been optimized as follows:
1. Realized two-way authentication. It not only provides the authentication of the base station to the MS, but also provides the authentication of the MS to the base station, which can effectively prevent pseudo base station attacks.
2. Provides integrity protection of access link signaling data.
3. The key length is increased to 128 bits, and the algorithm is improved.
4. 3GPP access link data encryption extends to the radio access controller (RNC).
5. The security mechanism of 3G is also extensible, providing security protection measures for the introduction of new services in the future.
6. 3G can provide users with security visibility operations, users can always check the security mode and security level they use.
7. In terms of key length, encryption algorithm selection, authentication mechanism, and data integrity verification, the security performance of 3G is far superior to 2G.
However, these 3G security mechanisms are only limited to the wireless part. For the wireless enterprise network based on 3G access, the security of the wireless part is far from enough. It is necessary to ensure the security of data throughout the transmission process, that is, end-to-end safety.
3G router access security deployment
With the development of 3G data communication applications, professional data communication manufacturers in the industry have launched 3G security routers, which can well solve the problem of 3G network data security transmission. The following uses an example of the application of the 3G security router in the financial off-line ATM as an example.
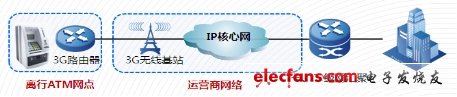
Figure 4 3G access
As shown in the figure above, the financial ATM outlets use 3G routers to wirelessly access the 3G wireless network, and connect the financial level 1 or level 2 network aggregation routers through the operator's 3G wireless base stations and IP core networks to realize the ATM and financial level 1 Internet or secondary network business exchange visits.
According to the application mode, 3G access security deployment is based on the following considerations:
Access authentication security
It is required to provide multiple identity authentication binding functions based on user name, password, and IMSI (internaTIonal mobile subscriber idenTIty, international mobile user identification code) when logging in to the 3G network, to ensure the uniqueness of the access user and prevent illegal users from using the 3G network Access the user's private network.
End-to-end privacy
In order to ensure the privacy of user services, the solution must be required to provide end-to-end private dedicated channels from branch 3G routers to financial or government industry first-level or second-level network aggregation routers to ensure that the branch services are private during the operator's network transmission process Sex.
Omni Microphone,Omni Directional Mic,Omni Directional Microphone,Omni Directional Condenser Microphone
NINGBO SANCO ELECTRONICS CO., LTD. , https://www.sancobuzzer.com
